STORY OF THE MONTH
The architecture of Quantum Key Distribution Network.
 Sep 2025
Sep 2025  Shashank Kumar
Shashank Kumar
In my last story, “Weaving the Quantum Web: Bob’s Vision for a Connected Future”, I introduced Bob, an expert in quantum-safe communication who envisioned a quantum network built on trusted node architecture. Now, let’s explore what powers that network.
When people think of quantum key distribution, they imagine qubits traveling through quantum channels
something mysterious and completely alien to everyday technology. The popular belief is that this system
generates unbreakable encryption keys that will remain secure no matter how technology evolves. But here’s the reality: it’s far more complex than just quantum mechanics.
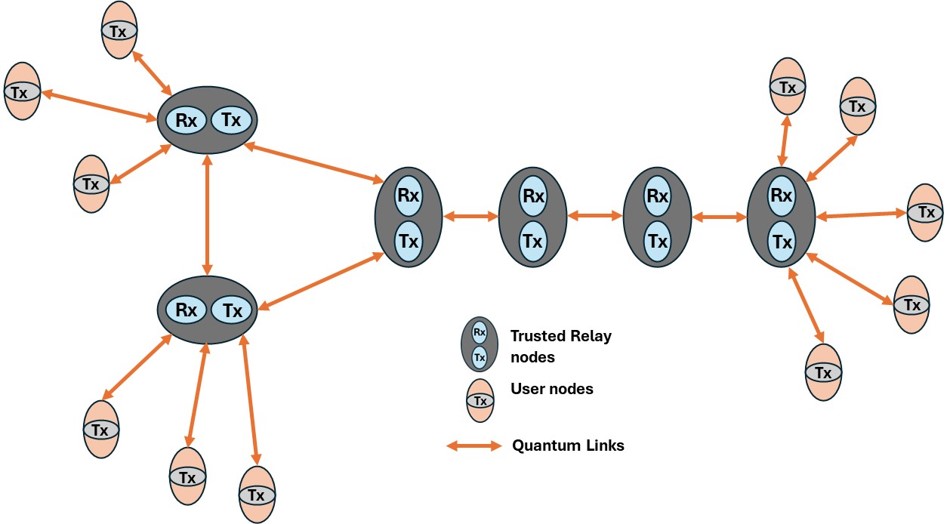
A functioning QKD network isn’t a single system, it’s more like an orchestra with multiple layers, each playing a specific role. After building one of the first operational quantum networks and collaborating with numerous researchers, Bob distilled the architecture into six distinct layers. Let’s walk through them.
Layer 1: The Quantum Layer
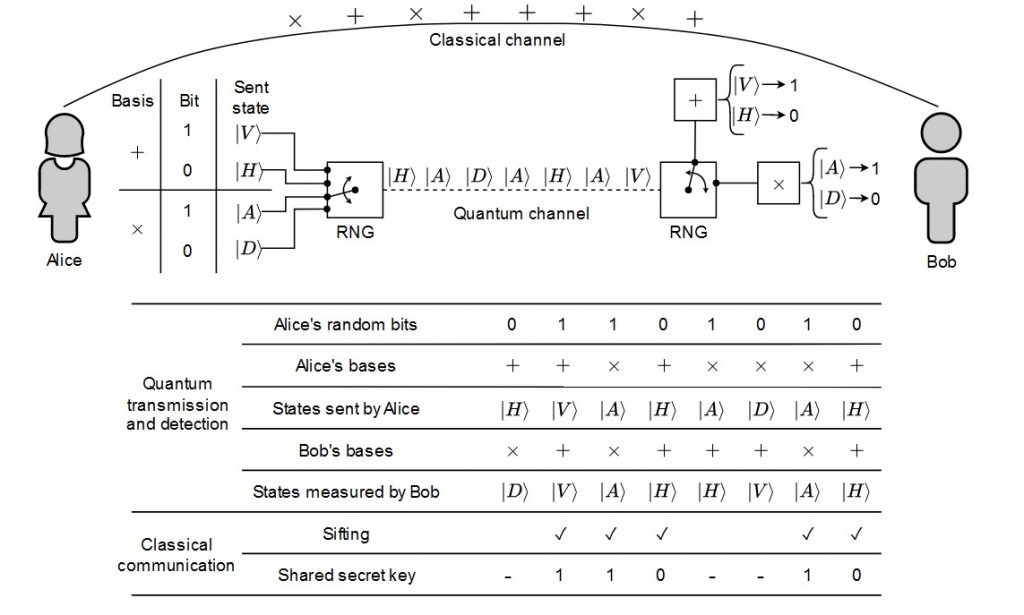
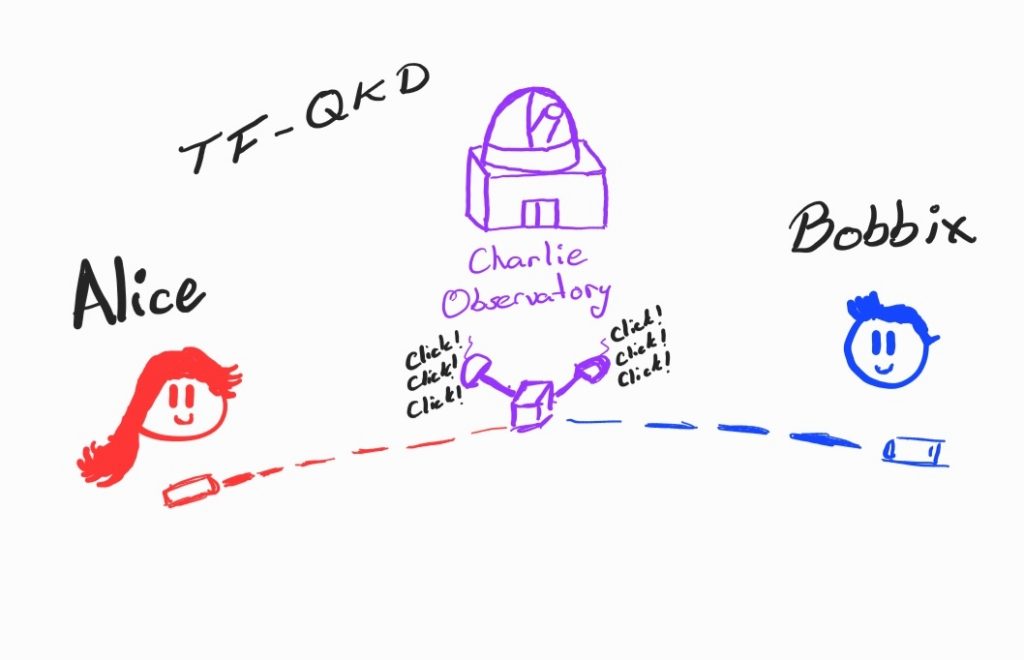
This is where the magic happens—the heart of any QKD network. Here, quantum principles generate actual cryptographic keys. The process involves transmitting quantum signals between distant parties and then measuring them to create shared keys. This layer handles quantum channel synchronization, key distillation, and uses random number generators to encode qubits. It also manages the optical switching and wavelength division multiplexing that keeps signals organized. Think of it as the engine room: complex, precise, and critical.
Layer 2: Key Management Layer
Once keys are created in the quantum layer, they need to be stored, moved around, and distributed where needed.
That’s the job here. This layer uses key management agents to store keys and set up end-to-end relay systems. It authenticates the keys and delivers them to applications that need them. If there are other cryptographic keys (like those from post-quantum cryptography), this layer handles those too. It’s essentially the warehouse and logistics center of the network.
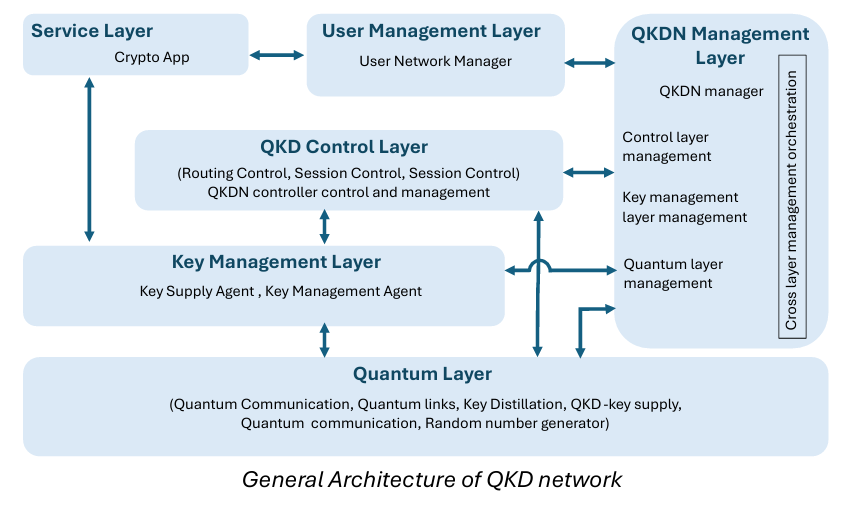
Layer 3: QKD Network Control Layer
If the quantum layer is the engine, this is the brain. It ensures the entire network operates securely, stably, and efficiently. The control layer manages sessions, decides which routes keys should take based on real-time network conditions, and keeps track of all the configurations. It also enforces quality-of-service policies, handles user authentication and authorization, and coordinates everything happening across the network. When something needs to be adjusted on the fly, this layer makes it happen.
Layer 4: QKD Network Management Layer
While the control layer handles operations, the management layer watches the overall health of the system. It monitors faults, manages resource configuration, tracks key usage for billing, and evaluates network performance. It also handles security tasks like authentication and key lifecycle support. This layer acts like a hospital’s diagnostic team, constantly checking vital signs and making sure everything stays in balance.
Layer 5: Service Layer
This is where cryptographic applications live, the software that uses the shared keys to enable secure communication between users. Users never directly interact with this layer; they simply use the applications that rely on it.
Layer 6: User Network Management Layer
The final layer is where users enter the picture. A network administrator here manages the user’s own network infrastructure (faults, configuration, performance, security, etc.). For an end user, this is as close to the quantum network as they get.
What Users Actually See
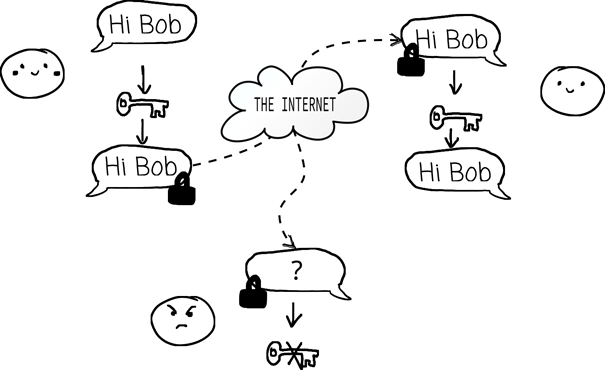
Here’s the interesting part: users only interact with layers 5 and 6. Everything else? Hidden. When a user requests a key, they see one simple outcome: two parties successfully exchange encrypted keys. The user trusts that the integrity is verified. But Bob understood what was really happening behind the scenes.
A quantum network isn’t just a beam of light traveling between two points. It’s a layered system where physics meets engineering, where routing intelligence combines with security protocols, and where human oversight ensures everything works together. As data flows silently through these interconnected layers, they work in perfect harmony, keeping information secure while remaining invisible to the end user.
Ref: For further details on the topic one can refer to https://www.itu.int/rec/T-REC-Y.3802-202104-I!Cor1/en
OTHER STORIES