STORY OF THE MONTH
When Eve Wins by Making Bob Go Quiet
 Aug 2025
Aug 2025  Loïc Millet
Loïc Millet
Quantum key distribution (QKD) promises information-theoretic security. In practice, clever eavesdroppers can exploit implementation imperfections to obtain information about the key. Here, we discuss a newly demonstrated attack on high-speed single-photon avalanche detectors (SPADs) that shows how such imperfections can leak nearly the entire key, and how careful design can close the loophole.
The idea
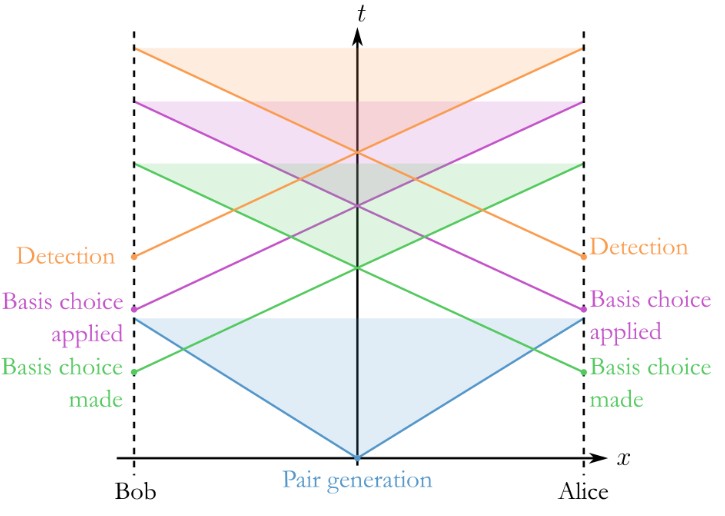
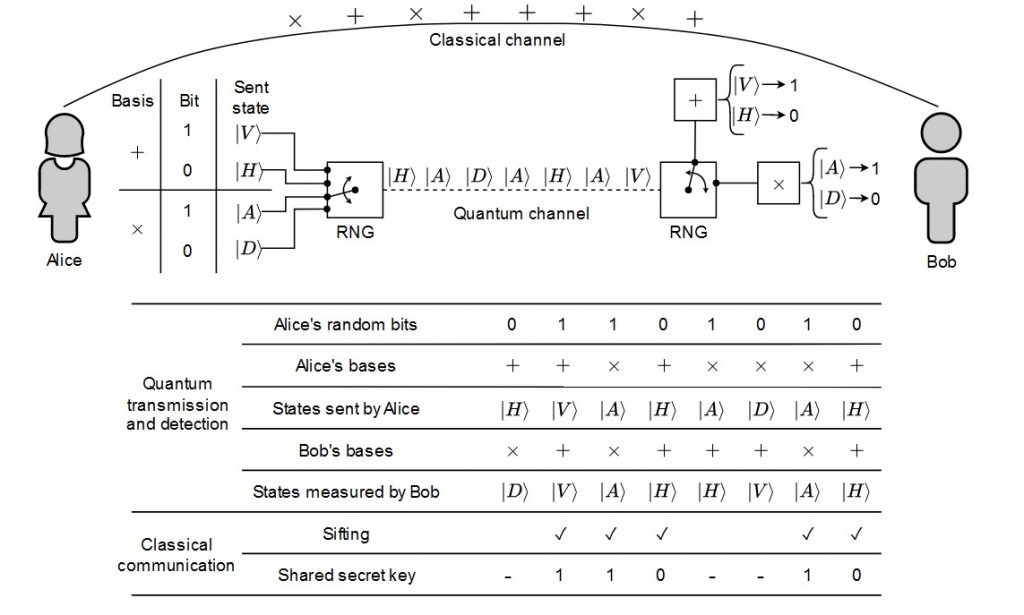
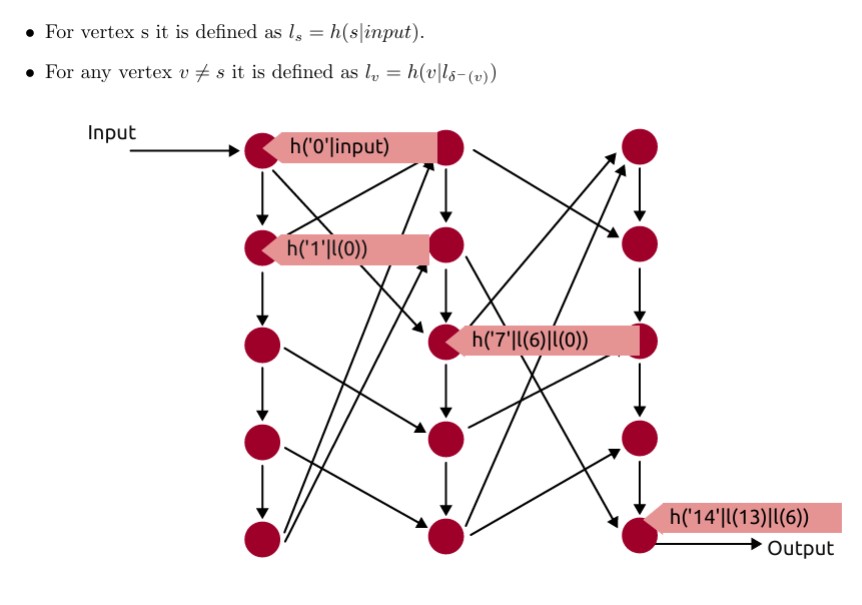
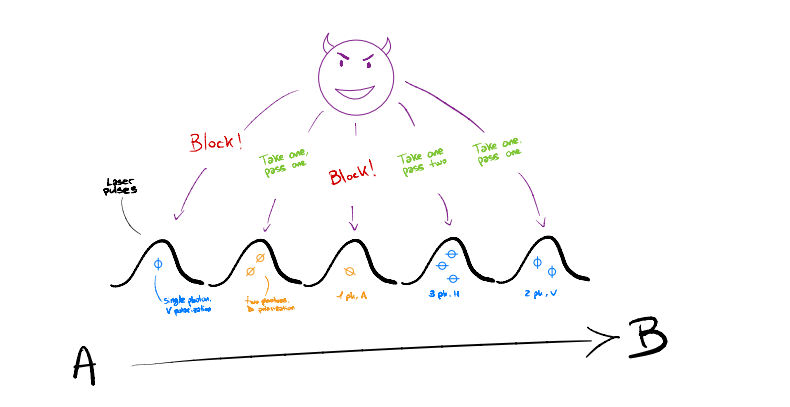
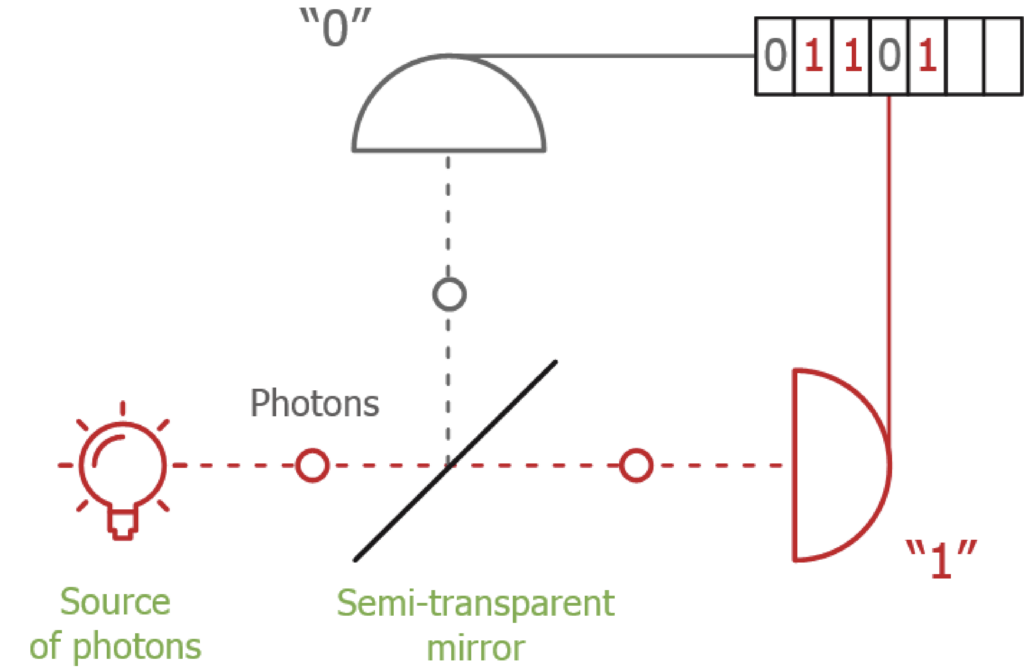
In a BB84 system using four polarization states and four detectors, Eve repeatedly pushes three of Bob’s detectors into continuous dead time so that, at any moment, only one detector can click. When Bob later reveals the basis for each detection during sifting, the fact that only a single detector could click lets Eve infer which qubit it was. Unlike the classic blinding attack, here the SPADs stay in Geiger mode.
How she does it
Modern gigahertz SPADs often include a width discriminator that discards abnormally wide avalanche pulses. Eve sends short “hacking” pulses containing hundreds of photons that trigger wide avalanches which the discriminator throws away (so no click is recorded) but still push the detector into dead time the brief recovery interval after an avalanche when the detector is insensitive. This dead time is the implementation imperfection she exploits. By timing the hacking pulses to the detector’s dead time, she keeps three of Bob’s detectors muted almost all the time. The only detector left ready to click is the one orthogonal to the polarization Eve used in the matching basis. When Alice’s real photon arrives, only that channel is active, so any click essentially reveals the bit to Eve after sifting.
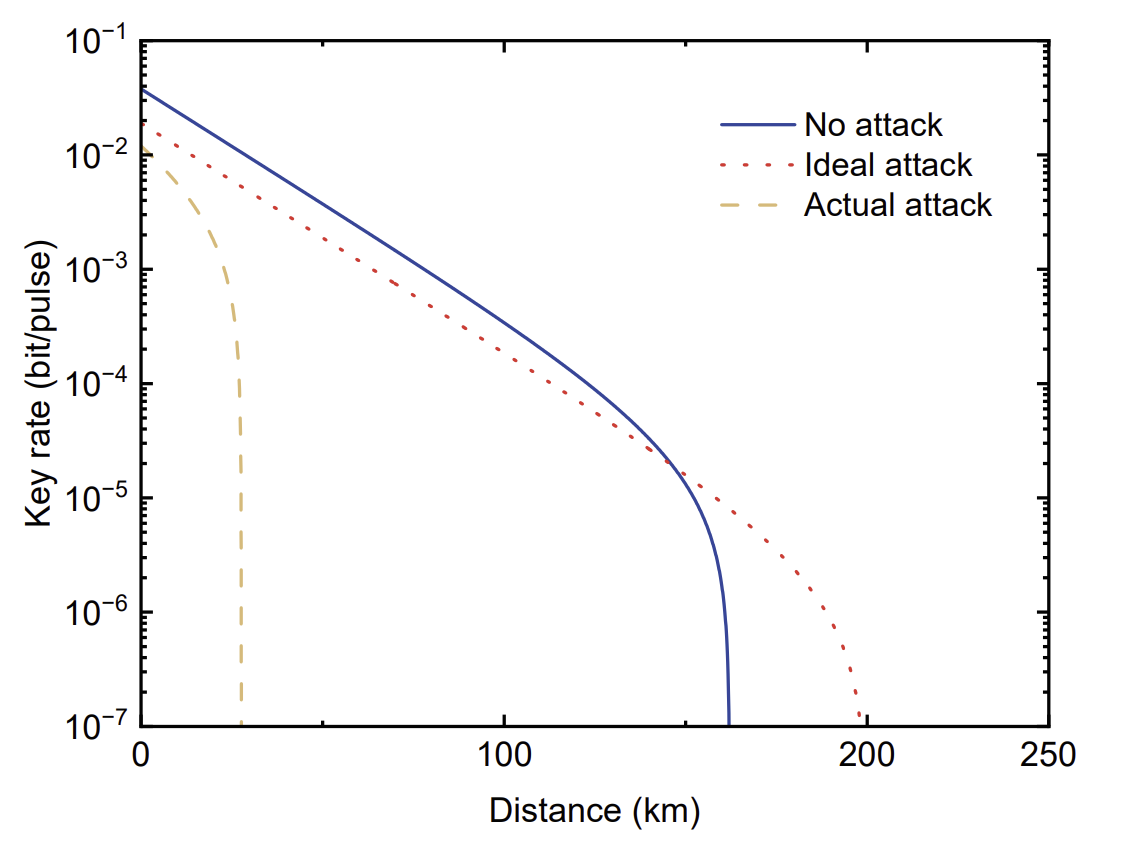
The key rate went up?
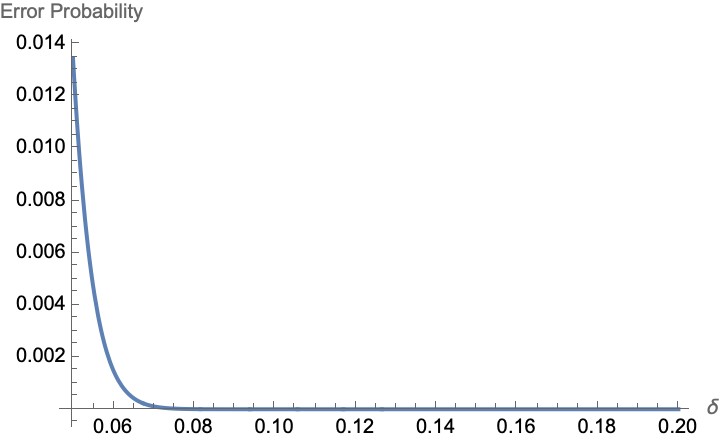
Here is the surprising part: in the idealized attack model, the simulated secret key rate (SKR) can look better at long distance. Why? Because forcing detectors into dead time also suppresses dark counts, which lowers QBER on very lossy links. In the authors’ simulation, the attack halves the short-distance SKR (since only ~25% of Alice’s useful events survive the muting), but it also extends the maximum distance by ~36 km because dark-counts are lower under attack.
Other imperfections bring back the errors
Real optics aren’t perfect. In practice, a small fraction of Eve’s hacking light leaks into the only active detector (roughly 1.5% in the author experiment). If Eve chose a different state than Alice, those leaked photons make the active detector click in error, inflating QBER and significantly lowering the SKR.
A simple fix
A simple engineering trick can protect against this attack: a common (global) dead time across all of Bob’s detectors. If any detector fires (or is forced into dead time), all channels become unavailable together, which removes the attacker’s ability to mute all detectors except one.
Source: “Muted attack on a high-speed quantum key distribution system”, https://doi.org/10.48550/arXiv.2506.03718, June 2025.
OTHER STORIES