STORY OF THE MONTH
Temporal Fixes: Time Travel, Data Leaks, and Cryptographic Remedies.
 Apr 2024
Apr 2024  Gina Muuss
Gina Muuss
January 2050, somewhere in Europe
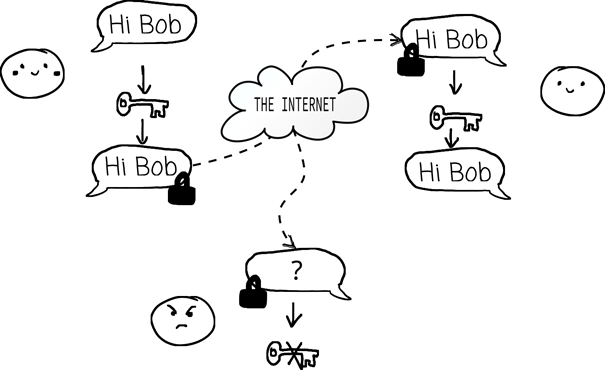
Angela is setting up the website for her new business. She is going to be the first to offer time travel at a decent rate with her company called Quantum Spacetime International: Time Trips for everyone. She builds a new database to save her users login data. For each user she saves a username and a password in clear text in a table. At 18:00, she leans back in her chair and presses enter. The servers spin up, and her users can finally create an account on her site and book their own curated time travel adventure.
February 2050, everywhere in Europe
Angela’s new service has taken off! Everybody and their robot-dog has an account on QSI and is traveling everywhen. People were in such a hurry to sign up that not everyone found the time to think of new passwords and some just reused ones they already used for other services. All news outlets want to interview Angela about her business, she does not get a silent minute for the entire month between giving interviews, implementing new features for her site and meeting with new business partners.
March 2050, in a dark basement
Not everyone is enjoying the new-found opportunities in travel. Ares, at least that is what he calls himself online, decides to look at Angela’s new site, but not to book travel; he tries to find a vulnerability to exploit Angela’s server. A few hours later, he did it! He managed to get into Angela’s database and now has an export of the users table. This table contains everyone’s usernames and passwords. Ares gets to work and tries the usernames and passwords at other services. After a few seconds his computer starts slowly beeping, each beep signifying a successful login into a service with the stolen credentials. He grins; just like he expected: Lots of people have reused passwords to book their time travel. Ares gets up to get himself some coffee and when he comes back a few minutes later, he can log into banks, e-mail accounts, video games and lots more.
March 2050, Angela’s living room
While Ares is wreaking havoc on the internet with his new-found power, Angela is on her sofa, wrapped in a fluffy blanket about to start the next episode of her favorite show. The first free evening in months, no of interviews and no technical work. Suddenly, her phone beeps. It’s her intrusion detection system, alerting her something is wrong. She immediately shoots up slightly tangling herself in her blanket. Finally, at her computer she identifies the problem: Strange requests seem to be leaking her usernames and passwords! Hastily, in her panic to react, she shuts down everything to stop the breach from going further, but she knows she is too late.
Ares already has all the data and Angela knows. She also knows that if the media get wind of this data breach her business is over. People trust her with their vacations and if she can’t even keep her database secure, how will she keep them save in the past and future? In her desperation, she calls her old friend Athy who directly offers to come over to help out.
Thirty minutes later, Angela’s kitchen
Athy arrives and the two sit in Angela’s kitchen contemplating on what to do next. While Athy was on the way, Angela managed to find the vulnerability, fix it and restarted the service. Users can once again book their time adventures and no further breaches should be possible. Still the damage is done and Angela knows she’ll have to inform her users about this. While she paints this very dark scenario on the wall, Athy interrupts her abruptly and says: “Wait, you are running a time travel business! You can fix this!”. Angela looks shocked, messing with time is strictly forbidden! When her guests travel she has specific safety guards in place to make sure no one can disturb the flow of time. Athy explains further: “You can just tell you past self to save only the hashed passwords, that is such a minor change nothing else will come of it, but the attacker won’t get the passwords! And only the people influenced by the change can feel it, so only you, me and the attacker, nobody has to know!” Angela draws in air between her teeth, she is still skeptical, but this plan is so nuts it might just work. But what did Athy say hash the passwords, what is that supposed to mean? Reluctantly, Angela agrees to the plan and asks: “Ok, let’s do this, but what do you mean by hashing a password?”
Another five minutes and the brewing of some tea later, Angela’s living room
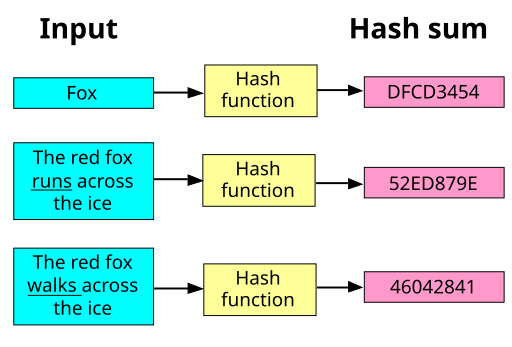
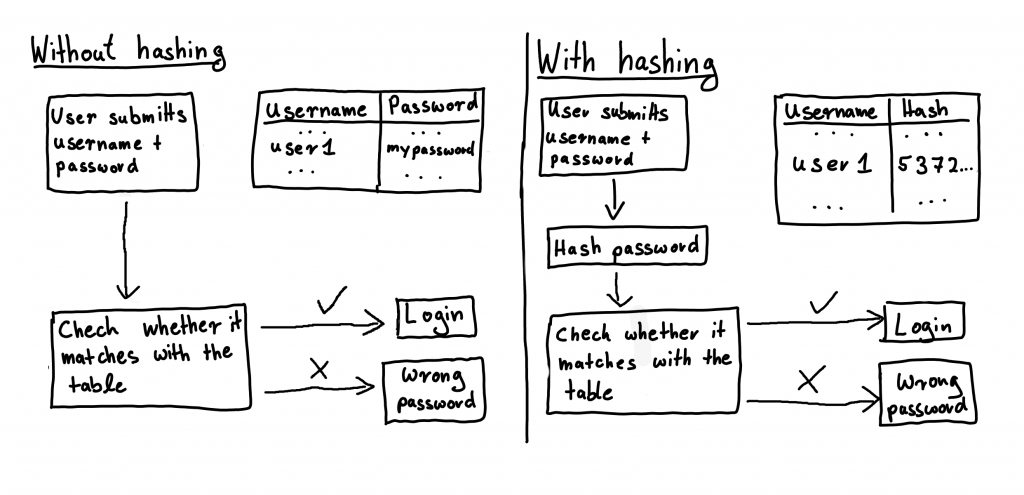
Athy has cleared Angela’s whiteboard and is explaining to Angela: “Look, currently you are saving the password in clear text, so if an attacker steals the database they get all the passwords. There is something called a cryptographic hash-function, it takes in some text; for example a password and mixes it up really well. This way from the result of the function you can’t know what the text was you put in. But each time you put in the same text or password you get out the same result, called a hash- value. Now instead of saving the passwords, we just save the hash-values. We can still check that the password is correct by computing the hash-value and then checking that it is the value we saved; but an attacker now only gets the hash-values when stealing the database.” Angela thinks for a few seconds and then asks: “But can’t the attacker then get the password from the hash-value?” “No, that is the fun thing about this cryptographic hash-function-thing. You can only find a text that has the same hash- value as one you have by trying them all.”, Athy goes on to explain. The next half of an hour is filled with Athy showing Angela in detail how to hash the passwords in her application until she is confident and ready to go to the past. They prepare the time machine, deactivating the safety features that would prevent Angela from interacting with the past. Angela gets in, the machine rattles and blinks, and a few seconds later Athy is alone in the apartment.

December 2049, somewhere in Europe
Angela lands in her own kitchen, or her past kitchen? She isn’t quiet sure, the linguistic detail of time travel are still highly debated, and she doesn’t remember what the latest results where. Wiping the thought away, she gets out of her time machine and goes directly to her office. She hesitates looking at herself from a couple of months ago, this is the evening she implemented the user authentication. Her apartment looks the same, but still different, that is her old chair; the first thing she replaced once she had the money to do so. She reminds herself of her mission, the longer she stays without the safety regulators on the more likely it gets that she is detected and that would land her in a lot of trouble. So she decides to get it over with and says: “Hey, don’t be afraid, it’s just me, mhh, you, well, us.” The younger Angela whirls around, looks at herself and shouts: “What are you doing? You’ll get us in trouble! You know you can’t interfere!” “Shut up, or do you want the whole neighborhood to know?!?
It’s important I’m here, so just listen!”, Angela goes on to explain what is going to happen if they don’t fix the code and how to use a hash-function to solve the issue. She doesn’t tell Angela about the vulnerability that lead to the breach in the first place. That would result in more disturbance in the timeline, and interfering like this is dangerous enough, she thinks to herself. Past Angela listens and agrees to change the code, and together they add hashing for the passwords in the database.
March 2050, Angela’s kitchen
Athy is still drinking tea and waiting for Angela to return, wondering why Angela invited them if she wasn’t going to be here. Suddenly, the kitchen started shaking, and the time machine appeared in front of Athy. Angela came out and excitedly asked: “Did it work?!?”. Athy looked at her like she was speaking Spanish, “What worked?”, they asked. Angela realized that if Athy didn’t know why she invited them it must have worked. The thief didn’t get to the passwords! She let out a relieved sigh, made some more tea and explained what happened to Athy.
March 2050, in a dark basement
Ares can feel it, someone changed time, and it affected him. It is a very distinct feeling of disorientation and the world shifting around oneself, he would always recognize it. He looked at his screen, suddenly all the successful login attempts were gone! “She’s a sneaky one, playing with time like that!” he thinks to himself looking at the database he managed to steal. He realized that all the passwords are now hashed, he knows that this means. Lots more work to make use of the stolen database. After a short walk, cursing time travel, Angela and the inventor of hash-functions he gets to work. He knows that in order to get to some passwords he will have to try all possibilities and check whether any of the hashes match. So he drafts a circuit board that does nothing but calculate the hash function for different inputs and checks whether the result is one of the values in the database. After a week he perfected the design and ordered thousands of custom printed circuit boards with his design. A short two weeks later, he is up and running, his basement now filled with circuit boards all constantly computing the hash-function and reporting to him when he found a valid password. Ares farm of circuit boards works, he gets a lot of passwords and people start reporting that their identity got stolen.
April 2050, Angela’s kitchen
Angela is sitting in her kitchen, nervously chewing on her sleeve. She invited Athy over to tell them that at this point so many people report issues that an investigation has been opened, and the police are trying to find out the thing all the victims have in common. So far they haven’t made the connection to Quantum Spacetime International yet, but it seems it is only a question of time. Athy finally arrives and Angela explains her worries of the police finding out that she has was the one who leaked the passwords without notifying anyone. They discuss for a long time what could have happened and how it could be that hashing the passwords is not yet good enough. They come to the conclusion that the attacker has to have tried all the passwords. “But this is always possible right? “, Angela asks defeated. “Well, there is one more option, there are memory-hard hash-functions. In addition to being difficult to find text that has a specific hash-value, it also takes some computer memory to compute the function or it takes a very long time. This way it gets more expensive to try all the values, like the attacker must have done for this, and then we can win some time.” Angela agrees that this sounds like a good idea.
Maybe if she is lucky the attacker even gives up if trying all options becomes too hard, she thinks. So Athy and Angela prepare the time machine once again; they disengage the interaction safety regulators and set the time for the evening when Angela first went back in time. This time Angela enters equipped with a description of how to implement the hashing of passwords using a memory-hard function. The machine whirls and Angela finds herself in her kitchen, looking at a confused past self and past Athy, that were just discussing how exactly to implement hashing in the application. Angela explains why she came back and that it is crucial that the application not only hashes the passwords, but uses a memory-hard function to do so. The three agree that past Angela will go to past-past Angela and explain to her. With a mission complete Angela returns to April 2050 and again meets Athy in her kitchen. “This should have done it”, she says, forgetting that she will have to catch Athy up again. After that is done they both decide to wait and see whether their most recent interference with time has solved their problem.
March 2050, in a dark basement
Ares was just about to design a circuit board to crack the hash-values from the database he just stole. There he feels it again, someone is messing with time again. Annoyed the looks at his database export again. “Really! A memory-hard function?!?”, he shouts angrily, “Now, just circuit boards won’t be enough. They will be so large, that if I get enough to actually get me some passwords I won’t be able to fit them in my basement, and also they will be so expensive that I won’t make any money from the passwords then!”. For a while he stares at the ceiling, should all this work have been for nothing? Then he remembers something a friend send to him recently, an advertisement for new practical quantum computers you can buy. So he gets back to his computer to buy himself one, in hopes that it will help him defeat the memory-hard function to crack these passwords once again.
Whether buying a quantum computer will actually help Ares significantly is not clear at this point. Will it actually be faster and/or cheaper for him? Answering this question is the main topic of my PhD project.
Authors note: The process of correctly hashing passwords is complicated and includes more nuance than presented in the story. If you have to figure out how to save passwords, without relying on time travel to get it right, always look up a recent technical guide from a reputable source!
OTHER STORIES