STORY OF THE MONTH
Introduction to Quantum Key Distribution and the primary challenge in establishing a global Quantum Network
 Nov 2023
Nov 2023  Matías R. Bolaños Wagner
Matías R. Bolaños Wagner
With the ongoing growth in the Quantum Computing field, the threat to our current asymmetrical encryption schemes is continuously looming. As previously mentioned, two solutions surfaced to try to tackle this threat: Post-Quantum Cryptography (PQC) and Quantum Key Distribution (QKD). My research area is on QKD, so let’s introduce what it is and how it is used before moving to specifics.
In Chapter 1, you read about symmetric and asymmetric encryption schemes, but for this, let’s focus just on one particular symmetric scheme, known as one-time pad (OTP). This scheme is known to be information-theoretically secure or unconditionally secure, which means that, if done properly, is uncrackable. Sounds pretty good, right? So why don’t we use this for absolutely everything?
Well, one-time pad comes with certain conditions, often difficult to meet in real-life scenarios. For instance, when Alice wants to send a message to Bob using OTP, they must share a key with specific requirements:
- The key must be at least as long as the message
- The key has to be random. Defining randomness and its properties can take an entire Story of the Month, so let’s just say for now that normal algorithm-based random number generators won’t do. A real random source is needed to provide the key.
- The key can’t be reused, both totally or partially.
- The key has to be, of course, kept secret.
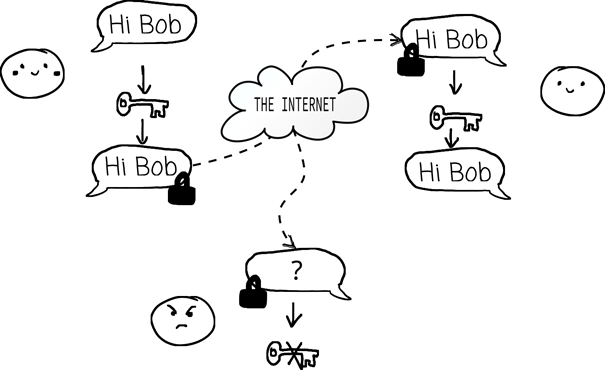
Now this just takes the key-exchange problem to a whole new level. This not only requires exchanging a secret key between the parties but doing so quickly and reliably to accommodate message lengths. Additionally, once a key is used, the information is destroyed, necessitating a continuous stream of key exchanges
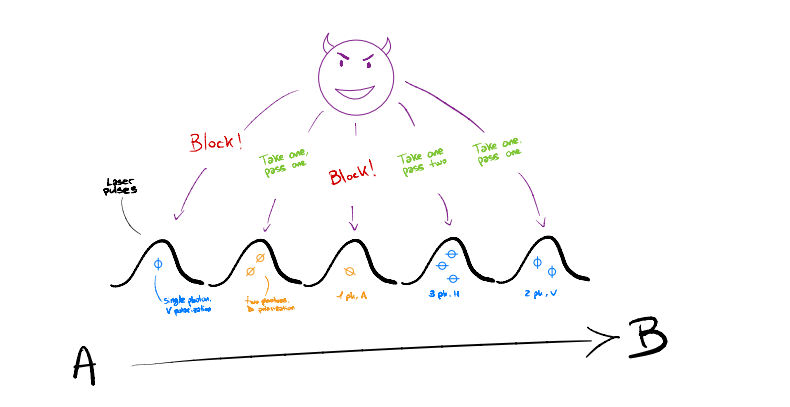
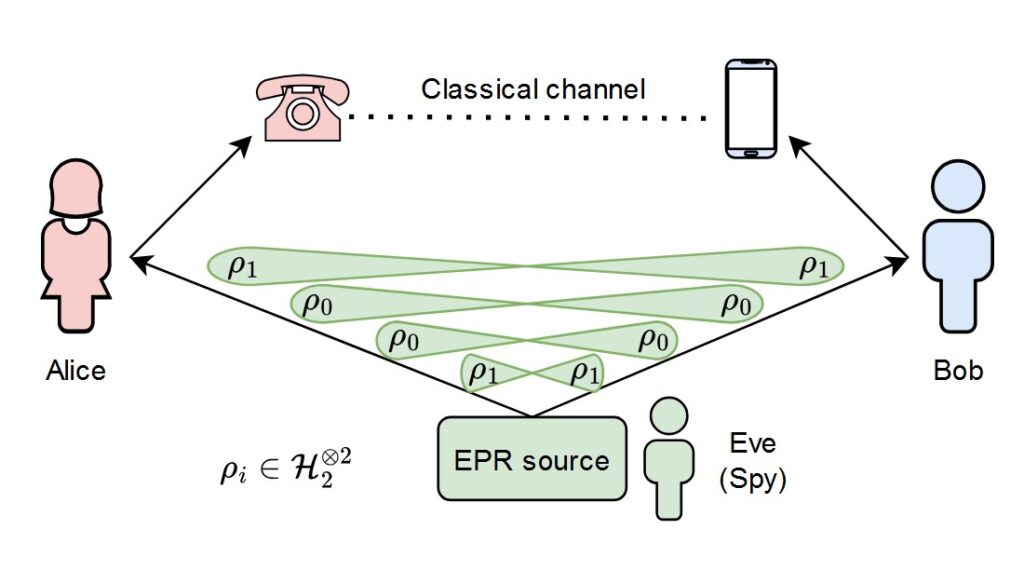
This is where Quantum Mechanics is dropped into the mix, with QKD providing a solution to the key-exchange problem, making implementing OTP somewhat feasible. Quantum Key Distribution represents a family of protocols to share a secret key between two parts, named again Alice and Bob, without the spy, Eve, obtaining relevant information on the key (so, exactly what is needed for an OTP implementation).
QKD’s main point is to encode the information of a bit into a quantum state (spin, polarization, energy levels, etc.) instead of a classical one (voltage levels). That way, we send the information of our key through a quantum channel. Thanks to the laws of Quantum Mechanics, if Eve tried to measure said quantum states, she would collapse the states into one of the bases she used to measure, giving Alice and Bob the ability to notice her presence because they would see errors on their measurements. This is not useful to send messages, because information is randomly lost, but is a great way to generate keys for OTP!
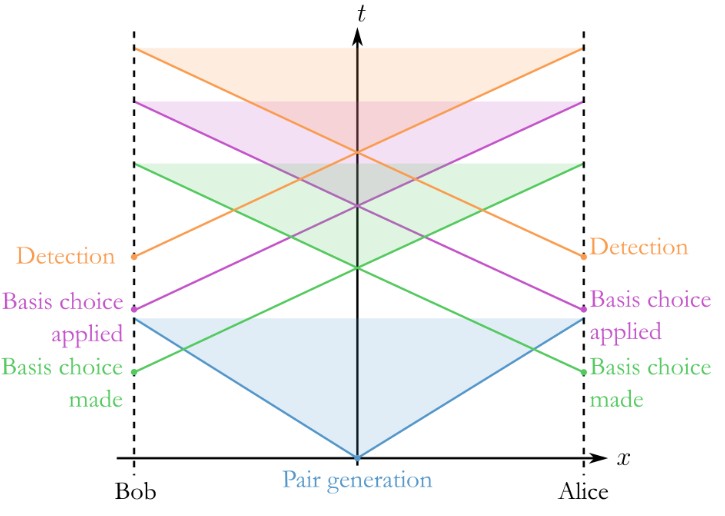
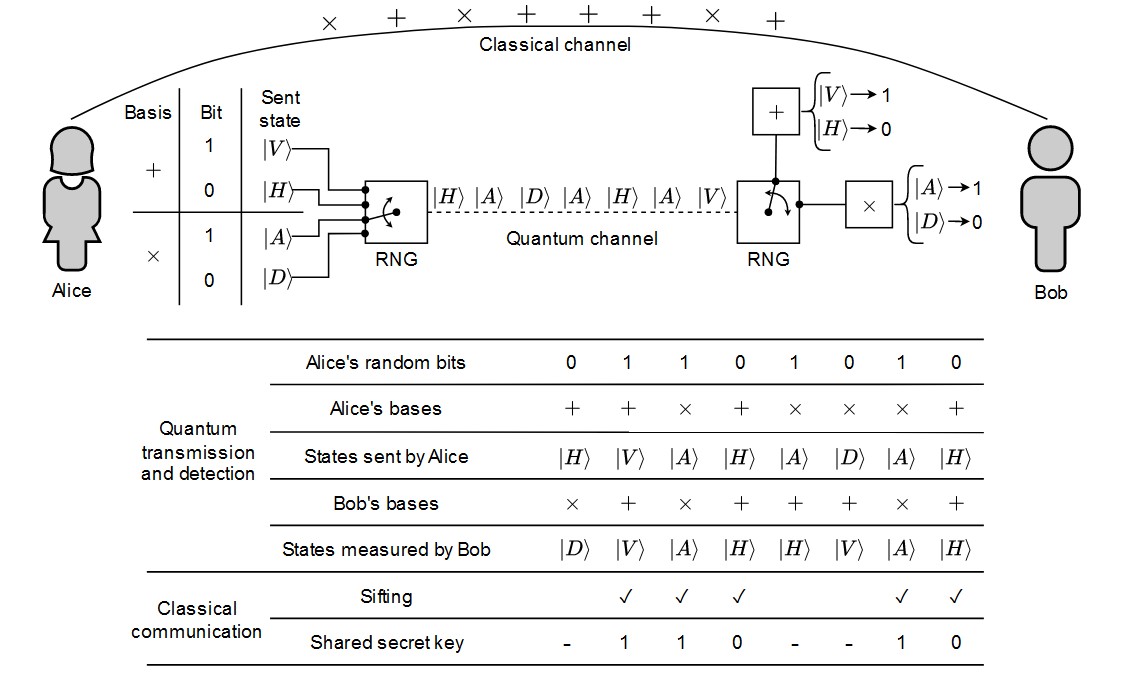
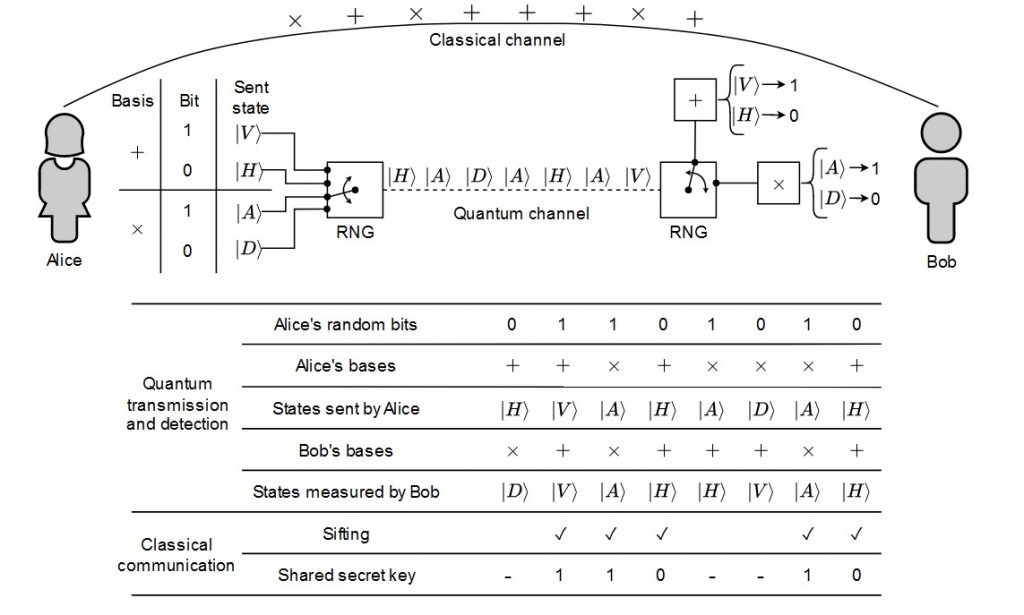
The first proposed protocol for QKD, called BB84, encodes the information in the polarization of the photon, since photons are great information carriers for long distance for a variety of reasons (I mean, you cannot get faster than the speed of light, just to name one). The protocol involves:
- Alice and Bob choose two mutually unbiased bases for encoding information, such as rectilinear polarization (H for horizontal, V for vertical) and diagonal polarization (D for diagonal, A for antidiagonal). Each one of these states corresponds to a bit value:
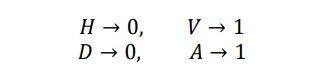
- Alice randomly encodes a bit into one of the bases and sending it to Bob through a quantum channel.
- Bob randomly chooses a base to measure each state. If the bases match, Bob gets the same bit sent by Alice; otherwise, the state collapses with a 50% probability into one of the two states used by Bob.
- Alice and Bob communicate through a classical channel, sharing the bases used for each state without revealing the results.
- They delete bits where different bases were used and keeping the rest as a shared key between them.
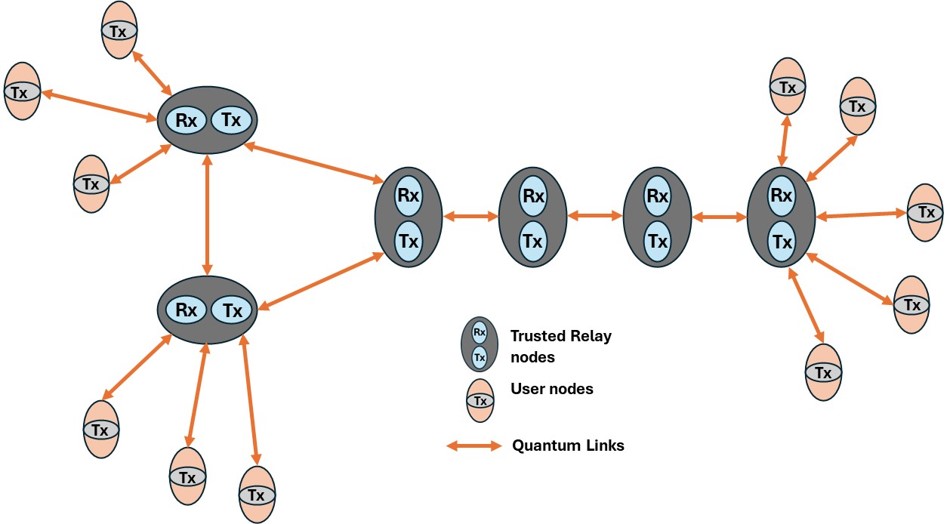
In the ideal world of the future, we need QKD to be a well-established scheme worldwide. However, a significant challenge in real-life implementations is channel losses. Over distances on the scale of thousands of kilometers, the losses on fiber are substantial, rendering QKD impossible to function. The current strategy involves short-distance QKD with fiber, which is well-studied and effective, and long-distance QKD with free-space links using satellites. The losses on the free-space channel are orders of magnitude lower than fiber, enabling a QKD protocol to work as intended.
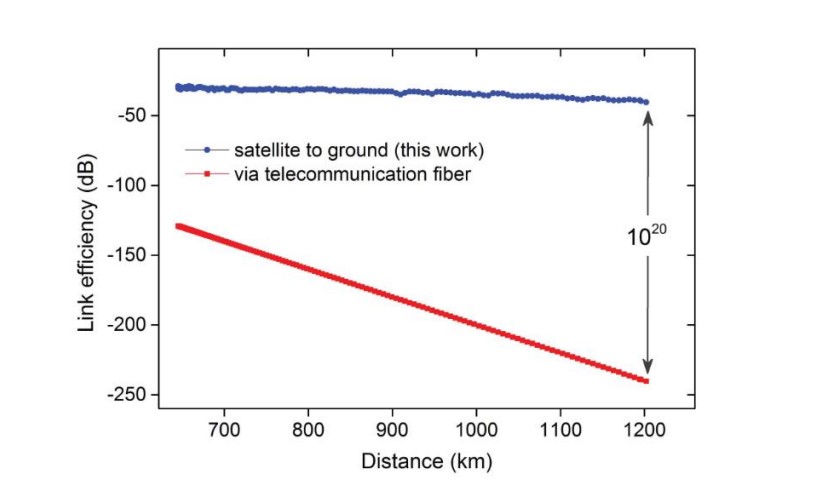
Figure 1. Satellite and fiber links losses. Sheng-kai L., et al. “Satellite-to-ground quantum key distribution”
While these two methods perform well individually, a worldwide network demands intermodal communication. This means fiber and free-space will have to be seamlessly integrated. Finally, after a lot of introductions, I finally managed to present my work topic.
Currently, my focus is on enhancing the efficiency of free-space to fiber integration, aiming to bring us closer to realizing a worldwide QKD network!
OTHER STORIES