STORY OF THE MONTH
Quantum Entanglement and its use in Quantum Key Distribution
 Nov 2024
Nov 2024  Matías R. Bolaños Wagner
Matías R. Bolaños Wagner
Imagine you’re holding a pair of dice. You roll one in New York and your friend rolls the other in Tokyo. To your astonishment, no matter how many times you roll, the numbers always match. This isn’t just luck; it’s something deeper and more puzzling. This phenomenon is known as entanglement, described by Albert Einstein as a kind of “spooky action at a distance”.
When two particles, such as photons or electrons, become entangled, their properties become linked. If you measure one particle, the other seems to instantly “know” what happened, even if they are separated by vast distances. This connection seems to occur faster than the speed of light. Although of course we cannot be certain of this, we can only say that our measurements, what we see every day in the lab, are pointing us in that direction.
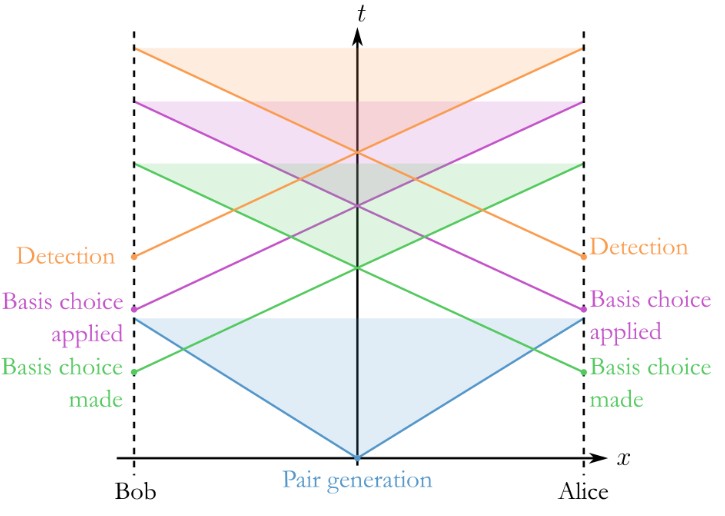
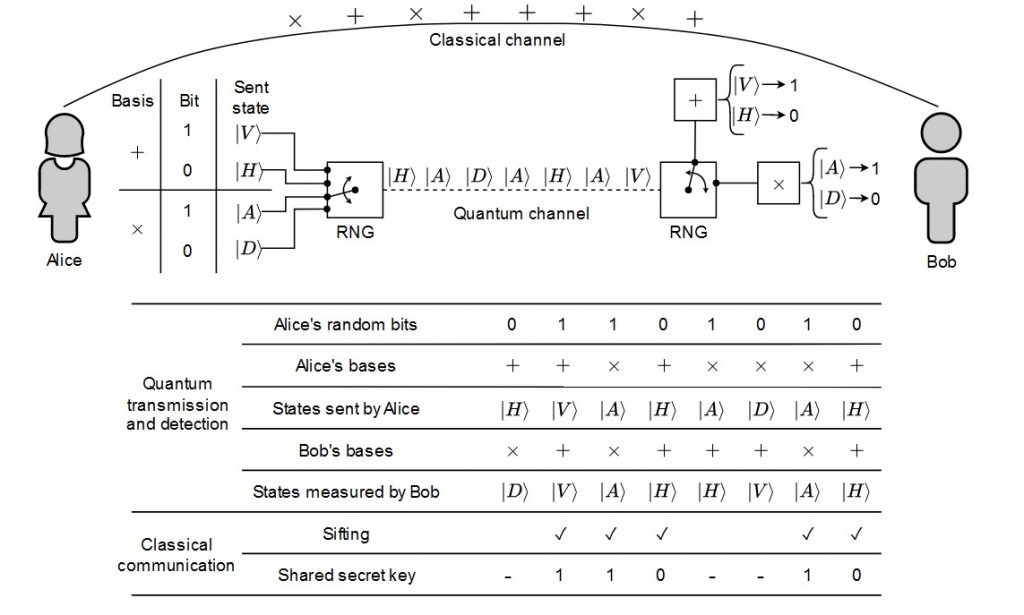
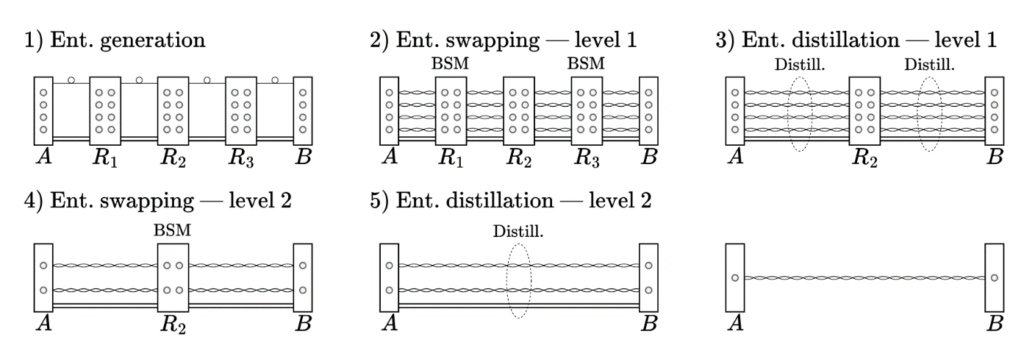
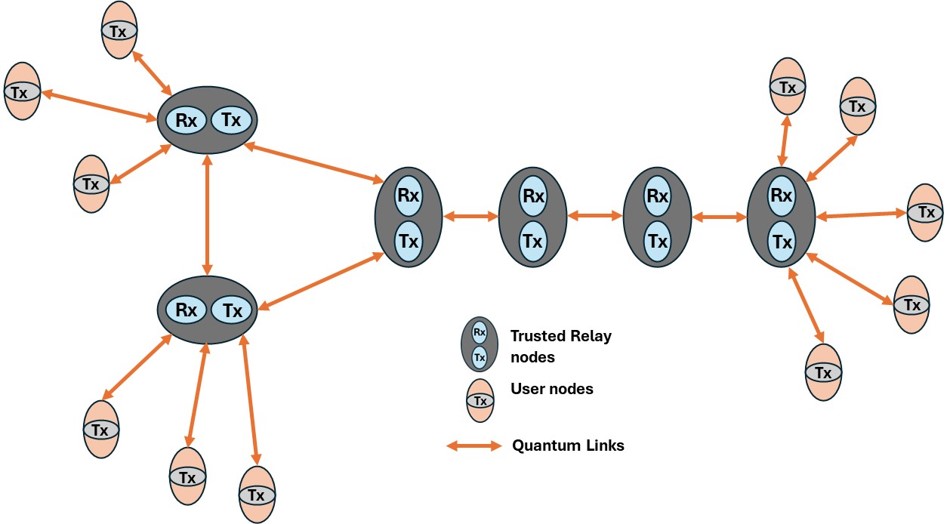
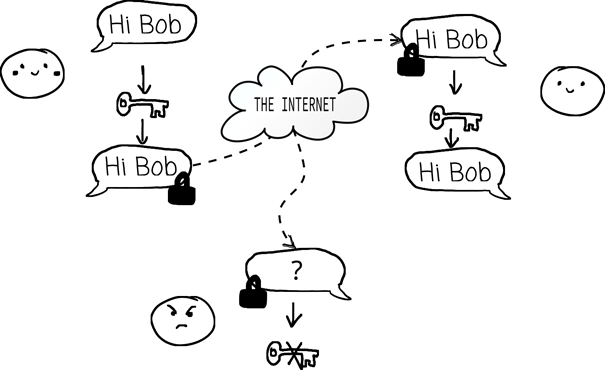
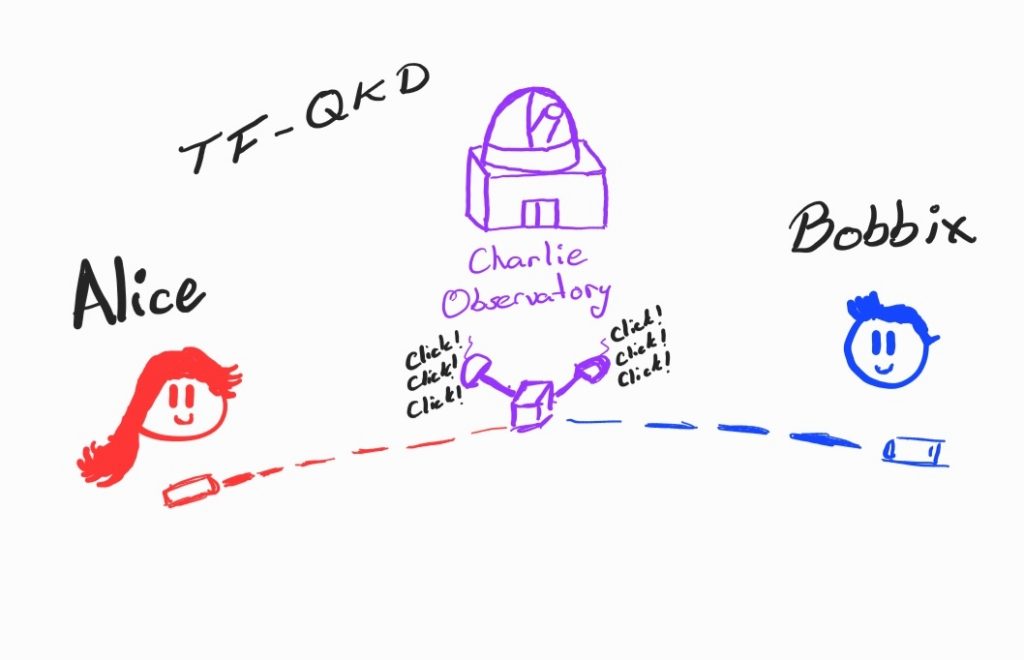
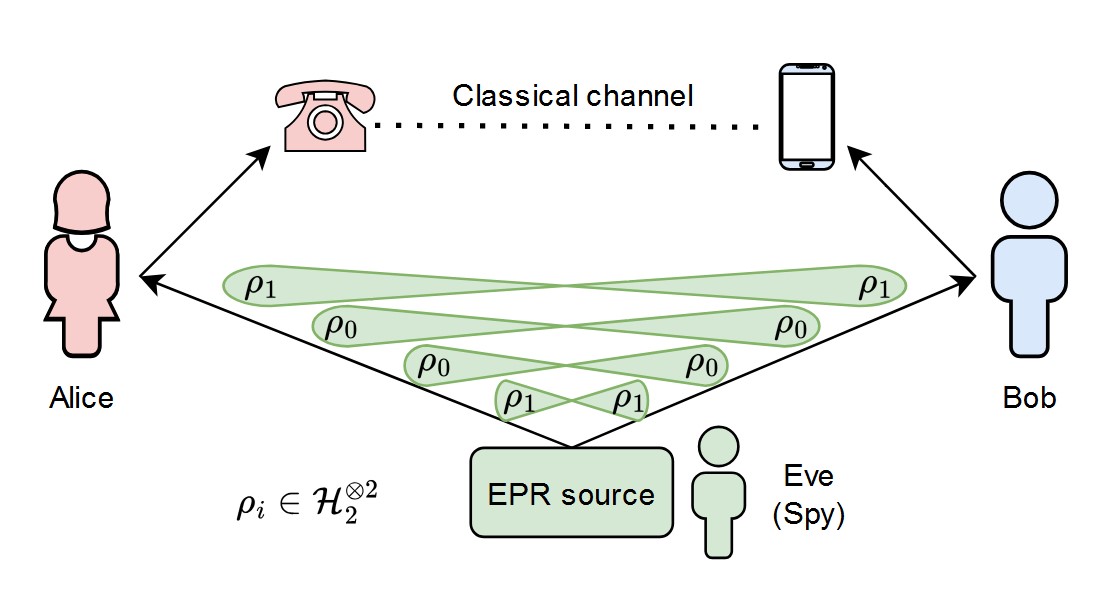
In QKD, entanglement provides the ultimate guarantee of security. The most widely studied entanglement-based QKD protocol is Ekert91, named after Artur Ekert, who proposed using quantum entanglement for cryptographic purposes in 1991. In this protocol, two parties (Alice and Bob) share pairs of entangled photons distributed by a central source. Each party measures their photons using randomly chosen bases, such as horizontal/vertical polarization or diagonal/anti-diagonal polarization.
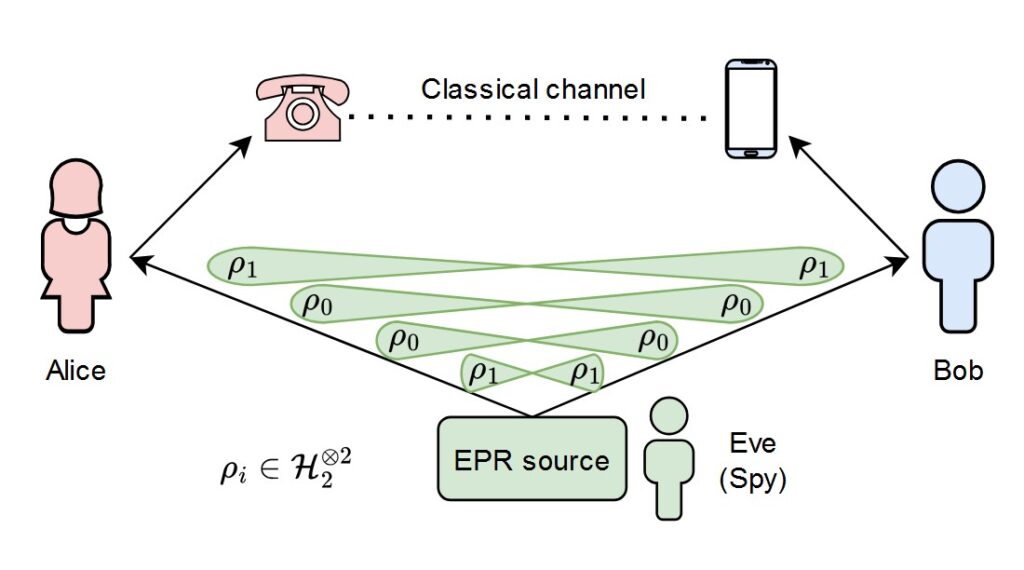
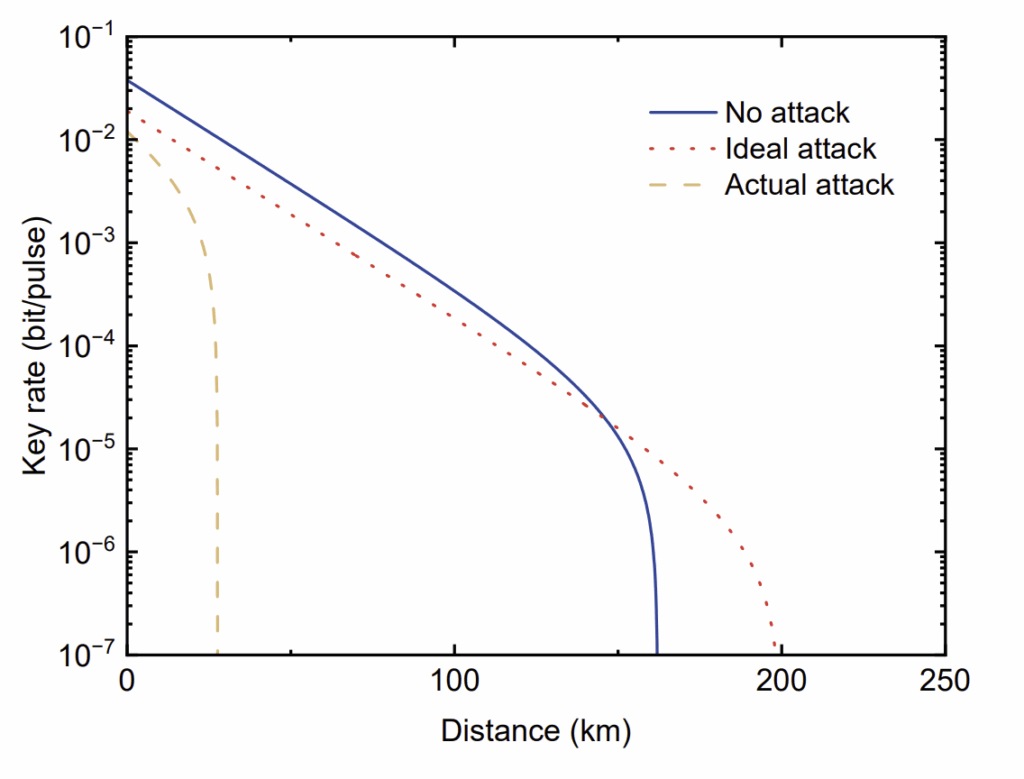
The measurement outcomes are strongly correlated due to entanglement. After exchanging their choice of measurement bases over a public channel, Alice and Bob can sift through their data to extract a shared key. Importantly, any attempt by an eavesdropper (Eve) to intercept the photons disturbs their entanglement, introducing detectable anomalies in the correlation statistics. These disturbances alert Alice and Bob to potential tampering, ensuring the key is only used when it is secure.
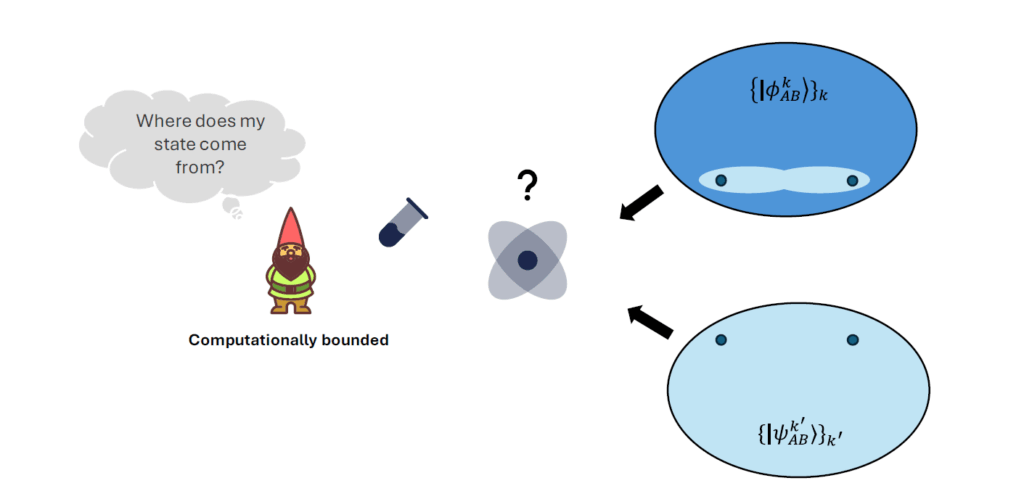
One of the remarkable features of entanglement-based QKD is that it doesn’t require Alice and Bob to trust the source distributing the photons. The security of the protocol relies entirely on the quantum correlations between the entangled particles. This makes QKD especially resilient against potential attacks, even if the photon source itself is compromised or controlled by an adversary. By performing statistical tests on their measurement outcomes, Alice and Bob can verify the presence of entanglement and ensure that the system is functioning as expected. This self-checking nature of the protocol adds an extra layer of confidence to its implementation, making it uniquely suited for high-security applications
OTHER STORIES